An overview of the Zero Trust Model and its applications for the Federal Government
With contributions from: Chris Dietz, Senior Director of IT
The core principle of Zero Trust is all users are assumed a threat until they can be verified. This may seem extreme, but when done right, Zero Trust employs strict guidelines to manage access to systems and data which can balance user experience and productivity with core security tenets creating an opportunity for modernization and enhancing security. Federal agencies are prime targets for attacks from bad actors and must balance security with the ability to execute mission – and deliver value – in a data-driven, distributed world. In this post, we’ll discuss how federal agencies can embrace a Zero Trust mindset to prioritize security while maintaining an agile customer service posture.
What is Zero Trust?
Zero Trust is not a product or solution. Zero Trust is a security model and framework that does not rely on the traditional concept of a network perimeter (think castle and moat) or trust zones. Instead, it treats every entity, whether inside or outside the network, as a potential threat and applies strict verification and enforcement mechanisms to prevent unauthorized access and data loss.
Zero Trust has a few simple principles:
- Least privilege access (the right data to the right people at the right time)
- Continuous verification
- Always verify
- Limit the “blast radius”
Zero Trust is based on “never trust, always verify” and uses multiple factors such as identity, device, location, behavior and other telemetry sources to determine the level of trust and assess risk for allowing access for each request and transaction. It relies heavily on proper encryption (e.g. FIPS 140-3) for all data in transit and at rest.
There are 5 primary pillars to Zero Trust:
- Identity
- Network
- Device/Endpoint
- Application
- Data
DOD has two additional crosscutting pillars to support the ingratiation of Zero Trust into their architecture:
- Automation/Orchestration Monitoring
- Visibility/Analytics
Why is Zero Trust important for the federal government?
The federal government manages critical and confidential data and systems that affect national security, public safety, and citizen services, making agencies rich targets for bad actors both internally and externally.
The complex and diverse IT environments managed by federal agencies, which include combinations of legacy systems, on-prem and cloud services, mobile devices (BYOD), and remote workers, make them rife for cyber-attacks and equally ideal for the tenets of the Zero Trust methodology. Additionally, federal agencies must comply with strict policy regulations, such as National Institutes of Science and Technology (NIST) Risk Management Framework (RMF) Publications or Federal Information Processing Standard (FIPS) encryption standards, which make the shift and culture change to a more secure operating environment necessary.
Some of the benefits federal agencies can generate by moving to a Zero Trust framework include:
- Enhanced security posture by reducing the attack surface, mitigating data loss, and detecting and responding to threats faster.
- Improved operational efficiency and agility by enabling secure and seamless access to data and systems, regardless of location, device, or network.
- Support for digital transformation and modernization of the agency by facilitating the adoption of cloud and mobile technologies aligned with the latest security standards and frameworks.
What are the challenges for Federal Agencies implementing Zero Trust?
One of the main challenges of implementing Zero Trust at a federal agency is the lack of a standards for this model. Agencies may have different definitions, requirements, and architectures for Zero Trust, which can lead to inconsistencies, compatibility issues, and security gaps. Moreover, implementing Zero Trust requires a significant investment in technology, training, and culture change, which can be difficult to justify and sustain in the face of budget constraints, competing priorities, and organizational inertia. In addition, Zero Trust policies cannot be broadly applied without due consideration to the behaviors and activities of an agency’s employees. Agencies must first conduct a comprehensive assessment of ways people want to work to understand how its employees execute their functions and collaborate with one another before they can create a successful strategy to migrate to Zero Trust architecture.
NIST released publication 800-207 that outlines best practices and recommendations on how to implement a Zero Trust environment for government. Federal agencies can utilize this publication to help establish a clear vision, strategy, and roadmap for adopting Zero Trust across its enterprise, as well as provide adequate resources, support, and incentives for its agencies to follow suit.
Three Steps to Get Started with Zero Trust
Assess Your Environment
Federal agencies have made significant investments in technology and want to make the most of their investments whenever possible. Doing an assessment of current capabilities and their maturity before making an investment in additional tools is extremely helpful and cost effective. Using the functional capabilities in Figure 5 of the DoD Zero Trust Strategy is a great framework to get started. Agencies should assess each capability area and whether the organization has the solution to perform or is performing that capability. If the agency is performing the capability, assess the maturity at which it is being performed. This assessment will allow organizations to understand what they are able to achieve with their current technology investments, at what maturity level, and if any gaps exist. A clear understanding of the AS-IS environment can help agencies develop a Zero Trust adoption road map.
Understanding the networks, interfaces, and applications that make up your agency’s enterprise architecture, along with clarity on the “ways of work” or “want to work” that occur within the agency, is critical step to shifting to Zero Trust. Without this context, a shift to zero trust can have a profound negative impact not only on agency productivity but also on the trust for internal IT support components.
With a clear picture of the environment to which you’ll be applying Zero Trust principles, an agency will then need to select its preferred Zero Trust best practices and define how the shift in its environment will occur. This is a deliberate step that requires consensus from key enterprise stakeholders, as it sets the groundwork for your Zero Trust journey.
Understand Your Data
Next critical step is to understand what normal looks like. Protecting data is the goal of Zero Trust, however, to protect data, you must know what it is and what where it is going. This may seem like a daunting task with that amount of data agencies create each day, but all data is not created equal. First, identify the most important and sensitive data which can be referred to as the “crown jewels”. This is data that if compromised or lost cannot be recovered, replaced or do great harm. Understand what it is, where it is, and where is it going. Baselining is essential, because if you don’t understand your data and your data flows, you will not understand when something is wrong or be able to react quickly. This is a potential use case for leveraging Artificial intelligence and Machine Learning.
Develop Your Methodology and Risk Thresholds
Zero Trust isn’t all about the technology; risk measurements and methodology must be developed and adopted to help determine when and what policies to trigger. Before you start implementing and enforcing policies it is important to understand the data sources and telemetry available to you, so you can run through specific use cases and develop risk thresholds so in the event of a breach, proper action can be triggered.
As a result of legacy technology, there may be constraints causing different methods of authentication. Each of these methods of authentication have a different level of risk. For example, multifactor authentication has a lower risk than username and password. This combined with other factors regarding network, device disposition, and application telemetry add up to a trust score. Depending on what the target is attempting to access, your risk threshold can decide whether to allow, limit, or disallow access in an on-going fashion rather than a one-time event check. If at any time the factors add up to a score that breaches a threshold, appropriate risk mitigation actions may be taken. Figure 1 is a simplistic example of this concept.
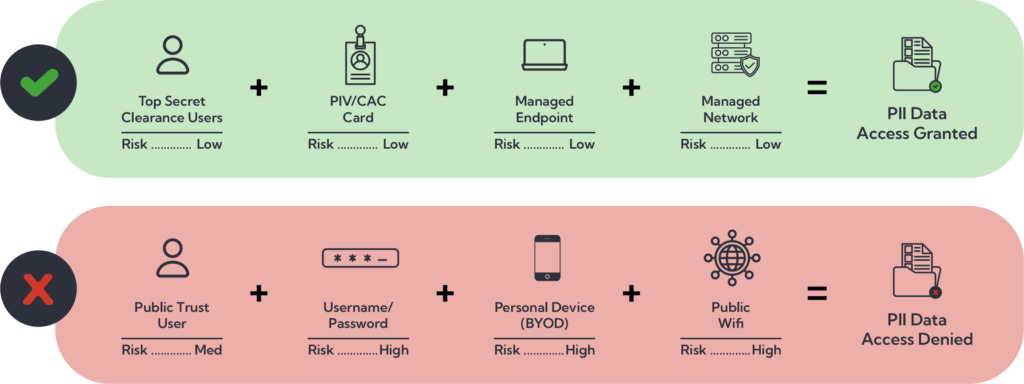
Figure 1
As a result, most data and telemetry must be assessed in an automated, on-going fashion. A crawl, walk, run approach is suggested before going straight to enforcement to ensure optimal outcomes are met when a threshold is breached.
There are many interpretations and definitions of Zero Trust and not all of them are true to the key principles. If you are interested in adopting Zero Trust at a federal agency the following recommended sources of reading and references to consider:
- Executive Order 14028: Improving the Nation’s Cybersecurity
- ZeroTrust.cyber.gov
- NIST SP 800-207
- Department of Defense Zero Trust Strategy
This introductory blog only scratches the surface on Zero Trust. Next time we will start doing a bit deeper dive into the pillars, starting with the Identity Pillar first. RIVA stands ready as a partner for anyone wanting to pursue the journey. If you are interested in learning more about RIVA’s approach to Zero Trust, reach out to Vice President of Cybersecurity, Gerald Caron.





