Embracing a Zero Trust Mindset
October is Cybersecurity Awareness Month and at RIVA, there’s one topic that stands out as mission critical to cybersecurity efforts both internally and for our government clients: Zero Trust. Did you know that there are hundreds of thousands of attempted cybersecurity attacks against government networks every day? Prompted by recent attacks on government agencies, the White House has requested $9.8B to bolster federal cybersecurity initiatives in 2022—up from $8.7B in FY2021 and in addition to $2B in funds already received. Cybersecurity threats also led to Executive Order (EO) 14208, Improving the Nation’s Cybersecurity, signed earlier this year.
Embracing a Zero Trust mindset is key to meeting the directives of the EO and staying proactive against evolving and increasingly sophisticated cybersecurity threats. In this blog, we take a look at what Zero Trust is, how it works, and some ways you can embrace Zero Trust to better protect your organization.
What is Zero Trust and how does it work?
Zero Trust is a mindset above all else. As RIVA’s Senior Vice President of Technology, David Callner, was quoted, “You can think of Zero Trust like Agile in that it is a philosophy. Agile is about being nimble and quick, putting the needs of the customer first, whereas Zero Trust is about assuming that an attack has already taken place. Everything from how systems are architected, designed, and developed is taken from the mindset that nothing can be trusted.”
Most experts agree on the following tenets of Zero Trust to guide organizational security measures, as highlighted in the figure below.
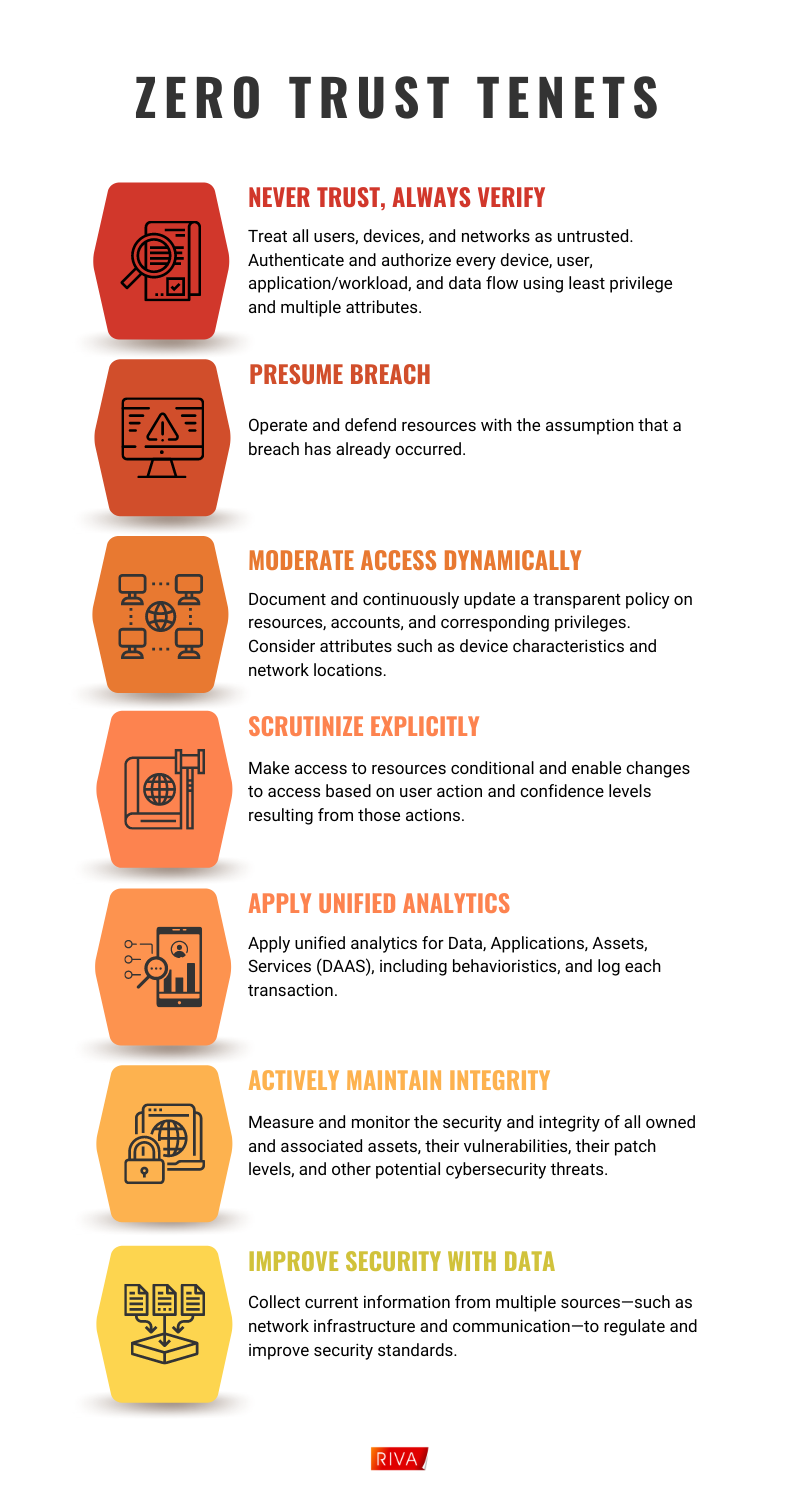
When architecting a Zero Trust system, start with the data—what you want to protect—and then look at how the data is accessed. As the name implies—unlike traditional approaches to cybersecurity—in a Zero Trust environment, no user, device, or network is implicitly trusted. User credentials alone do not gain a user access; in addition to credentials, the Zero Trust system also considers the device and network by which a user is attempting to access the system and what data the user attempts to access. Users can only access the data that they need to perform their jobs or certain tasks and must request to access additional data.
As an added layer of security, in a Zero Trust environment, the system will consider what data a user should be able to access based on how they’re attempting to access it. For example, if the user credentials are correct and the device is known, but the network is not known, the system may grant the user access but limit that access to data that is considered a low security risk. \
It might sound contradictory, but the goal of Zero Trust is not to prevent threats and breaches. Instead, the goal of Zero Trust is to limit the severity of a breach. In an environment protected by traditional security methods, a hacker typically enters the system undetected since their means to do so were implicitly trusted by the system. As a result, the hacker has more time to move through the system undetected and is not limited to one area within the system. In this case, the defender loses time to detect and react to the breach, and often—as we saw with the Colonial Pipeline Hack—the severity can be widespread through the system with drastic effects.
Zero Trust assumes that a breach has already happened to address threats quickly, in real time. Zero Trust accomplishes this goal in a couple of key ways:
First, since no user, device, or network is trusted and must always be verified, a hacker’s entry into the system is automatically identified and flagged as suspicious. This gives defenders more time to shut down and quarantine the device.
Second, even if a hacker breaches the system, they enter in a constrained environment and are, therefore, limited on how much data they can access. As a result, the breach is automatically isolated, and the defender can mitigate any damage quickly.
Zero Trust is most effective when it’s consistently applied. When every individual in an organization embraces a Zero Trust mindset —from executive leadership approving cybersecurity budgets and resources, to workers at the bottom of the organization who need to be conscious of how they access the system—data is better protected.
How can you embrace a Zero Trust mindset?
RIVA’s Senior Vice President of Technology, David Callner, recommends focusing organizational efforts on building knowledge, consensus, and intellectual property:
- Knowledge. Internal users’ daily habits can contribute to the frontline defense against cyber threats. Invest the time and resources to educate every employee—both IT and non-IT staff—on the tenets of Zero Trust to minimize easily avoidable risks to system security.
- Consensus. Consensus from different groups within the organization is critical to changing the culture around how security is handled across your organization. Build coalitions of staff who understand and exemplify the Zero Trust mindset.
- Intellectual Property. Incorporate Zero Trust tenets into your organization’s unique capabilities to provide secure services to your customers. Committing to this level of security is the true testament of an organization’s Zero Trust maturity.





